Phishing is a type of cyberattack in which criminals attempt to deceive individuals into revealing sensitive personal information, such as passwords, credit card numbers, or Social Security numbers. They do this by impersonating trusted entities like banks, government agencies, or well-known companies such as Apple, PayPal, or Amazon. The goal is to trick the victim into clicking a link, opening an attachment, or submitting private information through a fake website.
These phishing messages often create a sense of urgency or fear. For example, a message might warn that your account is about to be closed, or that unusual activity has been detected and immediate action is required. These scare tactics are designed to pressure you into responding quickly without taking time to verify the message’s authenticity. The links provided in phishing emails often lead to fake websites that look almost identical to the real ones, but are designed to steal your credentials.
There are several types of phishing. The most common is email phishing, which targets large numbers of people with a generic message. Spear phishing is more targeted and personalized, often aimed at specific individuals or organizations. Smishing refers to phishing attempts via text messages, while vishing involves voice calls that try to extract information over the phone. Another form, clone phishing, involves copying a legitimate email and resending it with malicious links or attachments.
To protect yourself from phishing, it’s important to stay cautious and skeptical of unexpected messages asking for personal information. Avoid clicking suspicious links or downloading attachments from unknown sources. Always double-check email addresses and website URLs for signs of fraud. Using two-factor authentication (2FA) adds an extra layer of security to your accounts. Keeping your software updated and being aware of common phishing tactics can also help you avoid falling victim to these scams.
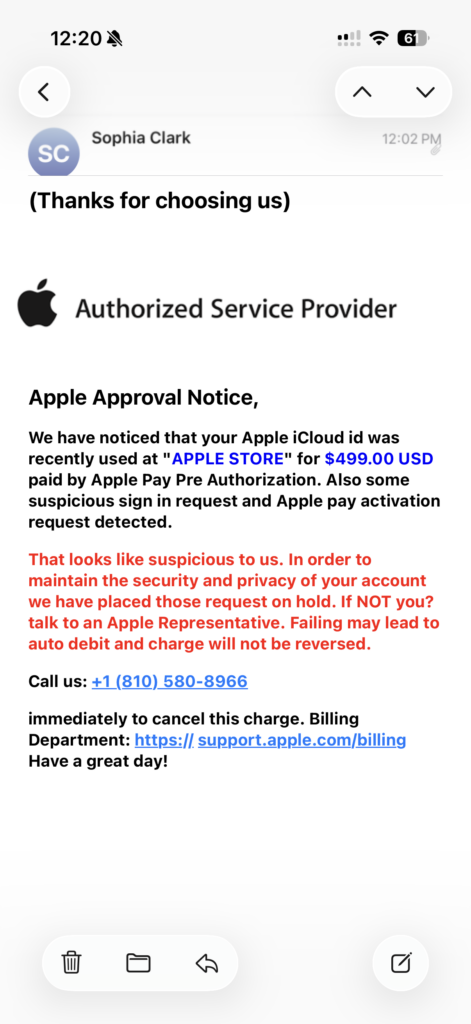
Scammers use a range of deceptive tactics to try to gain access to Apple accounts, often by manipulating trust, urgency, and a lack of awareness. One of the most common methods is through phishing emails. These emails are carefully crafted to look like official communication from Apple, complete with logos and formatting. They may warn you of suspicious account activity, billing problems, or an account lockout. Typically, they include urgent language urging immediate action, along with links to fake websites that closely mimic Apple’s login page in order to steal your Apple ID and password.
Another frequent tactic is smishing, or phishing via text messages. Scammers send alarming texts claiming that there’s an issue with your Apple ID or that someone has tried to log in from an unknown device. These messages often contain a link to a fake Apple site where you’re asked to log in, giving the scammer access to your account. Some even take it a step further by using vishing, or voice phishing. In these cases, the scammer calls you pretending to be from Apple Support. They may use caller ID spoofing to make the call look legitimate, then claim that your account has been compromised and ask for your Apple ID credentials or verification codes. They might even try to convince you to install remote access software or visit a fraudulent support website.
Scammers also use fake pop-ups or browser alerts that appear while you’re online. These pop-ups often look like system messages from Apple, warning that your device is infected or that your Apple ID has been locked. They direct you to call a fake support number where the scammer attempts to extract sensitive information. In some cases, attackers use social engineering—researching your personal information from social media or other sources to make their messages or calls more convincing. They may pretend to be a friend or Apple employee and ask you to verify your identity by providing login credentials or security answers.
Another technique involves triggering Apple’s legitimate password reset system. The scammer enters your Apple ID on Apple’s password reset page, causing Apple to email you a password reset link. Shortly afterward, the scammer contacts you via phone, email, or text—pretending to be Apple—and urges you to act on that email, tricking you into handing over control of your account.
Finally, some scammers create fake Apple Support websites that are nearly identical to the real thing. These sites often have chat features, contact forms, or fake download links designed to collect your personal data or install malware on your device.
To protect your Apple account, avoid clicking on links in unsolicited emails or messages. Instead, visit Apple’s website by typing the address directly. Always enable two-factor authentication (2FA) on your Apple ID, and never share your Apple ID password or verification codes with anyone, including someone claiming to be from Apple. Verify contact information using Apple’s official support site at https://support.apple.com, and report suspicious messages to Apple by forwarding them to reportphishing@apple.com. Taking these precautions can help you avoid falling victim to scams and keep your Apple account secure.



